Sourcing and Procurement
Breaking down IT to develop a robust cybersecurity framework
As cybersecurity threats increase in frequency, severity, and complexity across the world, it is crucial to understand the IT security requirements of an organization, and how they “stack up” against the risks. Often, attackers have been found to be residing within a company’s network months before they are detected. Simply implementing a tool in this scenario, is not a silver bullet.
As someone once said in a meeting, “a fool with a tool, is still a fool.” Harsh, but true! So, how can you ensure you are on the right path in developing a program to bridge the gap between the past, the present, and future threats? This article will look into the IT security market in detail and discuss the required underpinnings. Some of the important areas to look at while developing or refreshing your IT security programs are:
- Increase in BYOD and IoT
- Telecommuting or remote working
- Growing demand for outsourced, cloud-based cybersecurity solutions vs. in-house
- Stronger authentication methods and tools for accessing internal networks
The Growing Market
Typically, businesses rely on cybersecurity to safeguard their valuable data and information. Cybersecurity also emphasizes safeguarding of IT hardware, such as computers and networks from unauthorized access. As cyber threats have increased over time, security solutions have also evolved. Over the years, cybersecurity has helped organizations fight malware and phishing threats, using IoT and BYOD. This has acted as a catalyst for the increasing growth of the cybersecurity market. According to estimates by the Allied Market Research, the cybersecurity space will be worth $258.99 billion by 2025, considering a Compound Annual Growth Rate (CAGR) of 11.9% between 2018 and 2025.
Currently, key consulting and managed services players such as Accenture, Capgemini, Cognizant, HCL Technologies, IBM, Symantec Corporation, Tata Consultancy Services, and Wipro are front runners in the global cybersecurity market. Furthermore, a Gartner-backed article by eSecurity Planet lists the top 15 providers of cybersecurity products, services, and platforms are Fortinet, KnowBe4, Cisco, Splunk, Microsoft, IBM, Sophos, Palo Alto Networks, McAfee, Broadcom, Trend Micro, Check Point, ProofPoint, Imperva, and RSA (Dell Technologies).
Defining Business Needs
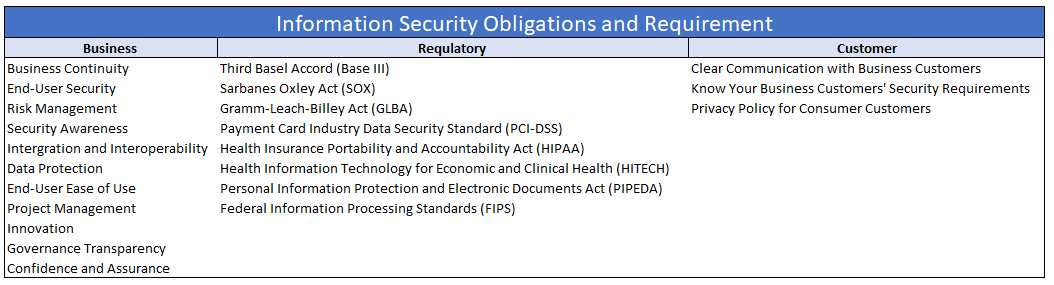
In a bid to develop an unassailable IT security strategy, it is important to evaluate an organization’s security requirements, to start with. This will require a deep dive into the anticipated requirements of the core business and customer needs. There are three broad levels in determining the right IT security fit for an organization:
- Business: IT requirements for businesses will primarily deal with commitments in securing valuable information and making it available on a need-to-know basis.
- Regulatory: Training the IT security infrastructure to adhere to regulatory compliance is crucial. It takes care of the legal, compliance, or contractual obligations of an organization. For instance, a healthcare company is obligated to comply with the Health Insurance Portability & Accountability Act (HIPPA).
- Customer: The organization’s IT infrastructure must keep customer requirements at the center. It can involve securing the blueprint files with encryption or ensuring zero data breach even outside the office network.
Benefits of Outsourcing
Despite the robust growth in cybersecurity infrastructure, several organizations are still not well equipped to manage it on their own. It is prudent to outsource the task to a reputable cybersecurity provider that can accommodate organizations of all sizes, which will also free up the company’s bandwidth to focus on core business. Such providers offer expertise from the aces of cyberspace law, along with proficient cybersecurity functions, risk assessment, and management, as well as guidance in auditing, compliance, governance, and policies.
Outsourcing IT security has the following additional benefits:
- Significant cost savings
- The minimum investment in capital expenditure
- Allows better focus on the core business functions and competencies
- Access to skills and expertise you may not have internally
Sourcing Best Practices
When outsourcing your cybersecurity services, it is important to keep the following points in mind, to ensure success:
- Get an assessment of your environment and situation, by an experienced and reputed cybersecurity company. Evaluate your strategic partners first.
- If something seems “off” with a company, it probably is. Look for companies with a solid track record and industry ratings. Beware of small boutiques and startups.
- If moving to the Cloud, it is important to know where the facility is going to be located, especially to evaluate geopolitical risks and legal requirements.
- Get references and follow up with them.
- Define all your requirement and make sure the provider can meet or exceed each one of them.
- Ask the provider about their internal and external audit and compliance processes.
- Get everything in writing, including email exchanges, bids, quotes, meeting notes, presentations, demos, etc.
- Make sure there are proper SLAs and penalties as a risk mitigation plan within an agreed contract, and how they plan to “make you whole” in a crisis.